I recently had a call with another company attempting to setup Autopilot following my previous post (Windows Autopilot with User-Driven Hybrid Azure AD Domain Join using Palo Alto GlobalProtect VPN). While speaking to them I learned that are currently using basic credentials (LDAP+RADIUS) with GlobalProtect and are only attempting to setup certificate authentication to get Autopilot working. They were still planning on having the user perform two-factor basic authentication after the Autopilot-based deployment. This configuration was the perfect use-case for GlobalProtect’s new “Use Connect Before Logon” functionality. This functionality was introduced version 5.2 and works by registering a Pre-Login Access Provider (PLAP). With PLAP you now have interactive access to the GlobalProtect client at the logon screen. A huge plus with this method is that it requires NO back-end changes to your existing GlobalProtect configuration. The functionality is completely client-side and only really requires an additional step during installation. This PLAP functionality works with basic credentials, certificates, and even SAML! I will be using basic two factor credentials below.
The first step will be to create a new GlobalProtect package in Intune. I am using the newest version below, 5.2.7. You can use the same steps for creating the package that I laid out in my first post, but we will be using an alternate wrapper script, InstallGlobalProtect_PLAP.ps1. InstallGlobalProtect_PLAP.ps1, will install GlobalProtect, set our default GlobalProtect portal, and register the Pre-Login Access Provider (PLAP). Everything else non-certificate related in my original post will still apply (ex. IntuneHybridJoinHelperInstaller.ps1).
Once the machine has been deployed you will notice an extra button in the lower right. This is the PLAP.
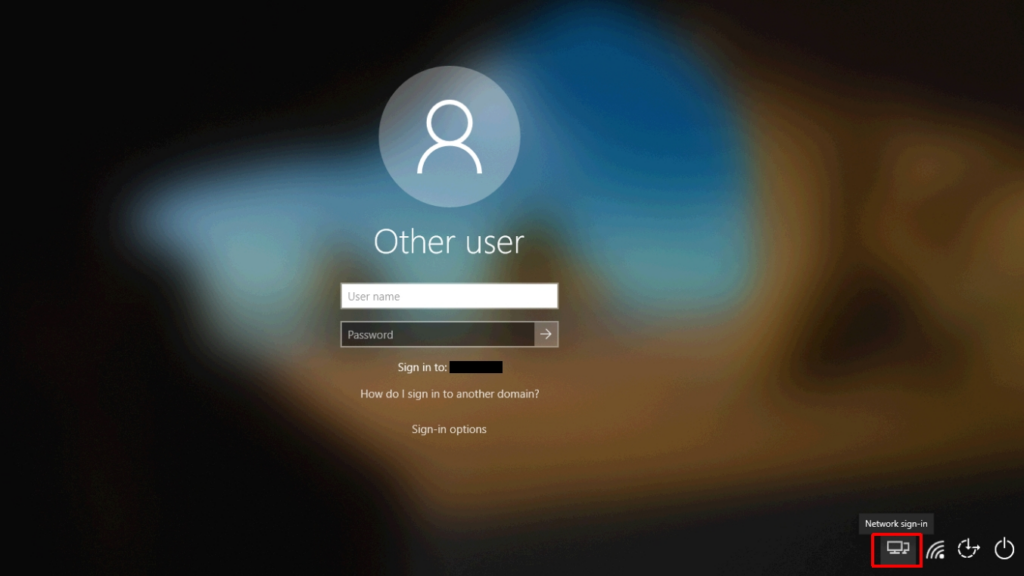
When clicked, GlobalProtect will attempt to connect to the portal configured in the wrapper script and you will be presented with a screen like the one below. The prompts here will vary based on your authentication method. Here I am being prompted for my LDAP credentials to authenticate to the portal.
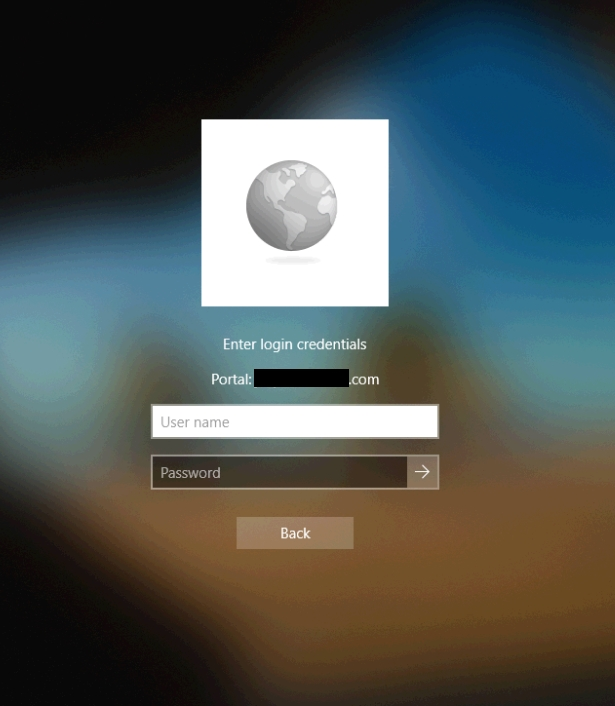
Once I passed the correct credentials here (and the correct second set of credentials at a second screen for two-factor) I was connected.
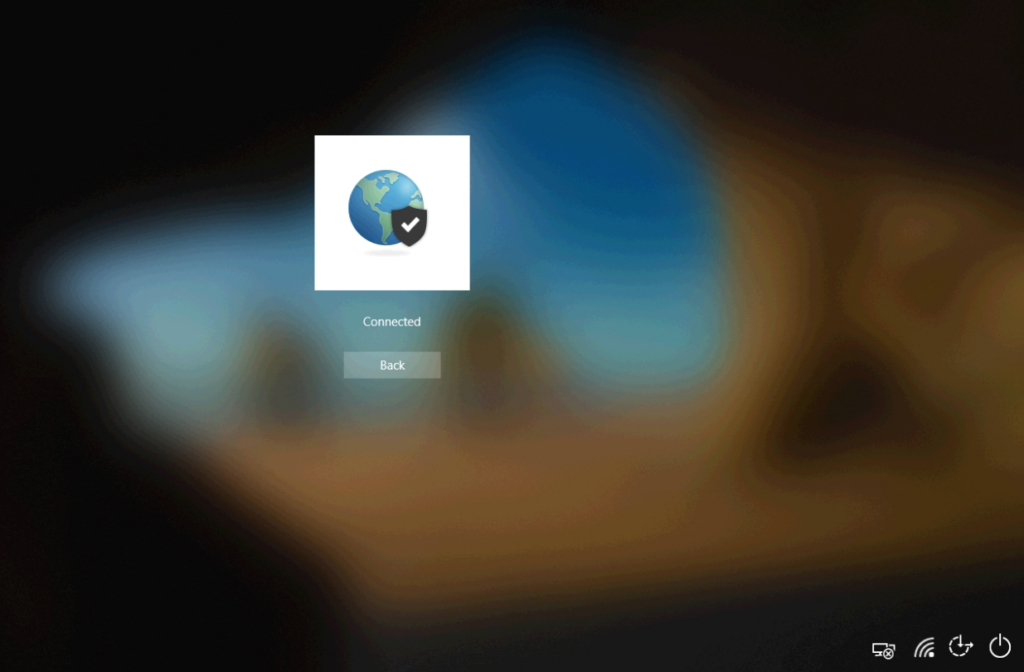
At this point you can click the ‘Back’ button and continue to log in to the device. That’s all there is to it! This is a great option for those of you who are lacking the desire to use certificates in your existing GlobalProtect configuration, but want to start using Autopilot.
Pingback: Windows Autopilot with User-Driven Hybrid Azure AD Domain Join using Palo Alto GlobalProtect VPN | Maniacal Methods
Thanks so much for “Part 2”!! This put the work back in my hands and cut the security team loose from the additional certificate work.
I only have one issue. The GP client attempts to connect upon login, after every reboot. It obviously fails since the client is now on the office network. Is this by design or did I miss something.
I’m glad this could be helpful!
So, one option for this is to configure internal host detection. This way GlobalProtect will detect you are internal to the network and won’t attempt to establish a connection (or will try to connect to the “internal” gateway if one is configured).
Hey Mark, I ran into an issue with trying to get this setup. I’ve experienced a different behavior when AP runs it compared to when it runs when your login. Its not putting the icon in the bottom right corner and it adds it to the signin options but does nothing. This is my first time trying to set it up and I am using version 5.2.6.
https://ibb.co/0QBVLxn Is an image of what I mean. Any help or insight is appreciated.
This is what GlobalProtect looks like if it is not installed with PLAP. Did you install it using the script I provided? In that script is a process that runs AFTER installation to enable PLAP (PanGPS.exe -registerplap).
If you have done this and are still having the issue then check the ‘(Default)’ registry value under: ‘HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\PLAP Providers\{20A29589-E76A-488B-A520-63582302A285}’. Verify that the value is set to ‘PanPlapProvider’. This registry should already be set if ‘PanGPS.exe -registerplap’ was already run.
Yes, I used InstallGlobalProtect_PLAP.ps1. I did not setup a deployment for IntuneHybridJoinHelperInstaller.ps1 as I did not think it was necessary after my results of just installing using InstallGlobalProtect_PLAP.ps1 with a fresh autopilot device that was off the network. What I do see is that the portal address is not entered for the device. I have a cisco gateway so I just logged in with that to see what happened.
It seems this is what failed for some reason. New-ItemProperty -Path ‘HKLM:\SOFTWARE\Palo Alto Networks\GlobalProtect\PanSetup’ -Name ‘Portal’ -Value $PortalAddress -PropertyType String -Force | Out-Null
Don’t see the portal address in the reg.
Might have something to do with how running in the context of System works. Completely my fault trying to cut corners. Feel free to delete my posts. Thanks for posting your two posts for GlobalProtect. This was great system engineering.
https://www.reddit.com/r/PowerShell/comments/30hvgv/script_wont_modify_the_registry_when_run_through/
Hi Mark – Great and very useful post. The only issue we have is with group polices that are not getting applied during the first time logon as we have enabled loopback replace mode. After we make a connection to VPN from the start up page and the user logs in we are seeing that specifically logon scripts and folder redirections from GPO are not getting applied. Any suggestions ?
Thakns,
Vinod
Yes! Please take a look at my original post (https://blog.markdepalma.com/?p=763). I wrote a helper script (IntuneHybridJoinHelperInstaller.ps1) that helps resolve many GPO-related issues. Scripts *may* actually kick off after the refresh using this. Folder redirection may only kick in the second logon because of how Explorer actually applies it (I’m not 100% there).
I’d love to hear your results after using the helper script. I’d be happy to look into enhancing it if either of those two settings still don’t work for you at first logon.
i followed what you did, and the device status shows as “Access is denied. (0x80070005)”
Any ideas? I did follow your original post, and than used this part so they can do username and password login.
Where exactly are you seeing this access denied message?
so i the whole restore of the laptop, and it onboards into autopilot/hybrid successfully, but i dont see the gp at login option. I check in endpoint.microsoft.com to look at the app status, and thats where it shows the access denied error msg. Not sure where i am doing it wrong.
Like your other posting, i do have the gpo deployed to that OU, and the machine name is successfully added in that OU i have it pushed too.
It does say its successfully deployed the Join-IntuneHybridJoinHelperInstaller as well.
actually i just tried again this morning, now it shows it successfully pushed out the “PLAP ” version i created based on this posting. As well shows what you have in your posting, but for it to work.
after onboarding finishes, and it goes to the login screen it still doesnt show. I had to wait i think about 15 mins, than restart the laptop and than it shows.
Do i need to do something else to have it show right away?
To really understand what is happening you’d have to look into the logs and timings. I suggest you run a new deployment, make a note of the time the deployment is done and you are the logon screen, reboot to get the VPN option to show, and then look at the PanGPS log file to see when the ‘-registerplap’ command was executed. Compare the time the command was run to the time the deployment finished and you first wound up at the logon screen.
is there away to make it so this gets run first before any other apps? I created a profile policy to create a local admin. When i login as a local admin, and all the other intune apps look to have been pushed except the GP one, but if i reboot than it install GP app it seems
I actually have a hunch that client is installing, but that PLAP provider is not active because this part of the OS has already been loaded. When you logon as local admin, do you see GlobalProtect installed and it’s just the option at the Windows logon screen missing?
so today, i redeployed the same laptop 3 times. 2 of 3 times it doesnt even show the gp app on the login screen, when i login as local admin, and i see the other apps pushed to it except GP. If i wait long enough i will see it installed on the laptop. This whole process i dont use ESP. Not suppose to use ESP right?
sorry forgot to mention, when it doesnt install right away, it shows as access deny when i check device install status. Do you know where i can check in intune to see what it says access deny?
Do you have a screenshot of what you are seeing? That would help to pinpoint the issue.
I had to manually set registry for the plap registration when installing GP 5.28. However, I’m being prompted for first set of credentials, but 2nd factor doesn’t display at login screen and then get error connecting. Any ideas?
Shouldn’t have to do anything in the registry manually if you’re running ‘PanGPS.exe -registerplap’ as part of the installation.
What exactly do you mean by 2nd factor? What type of authentication are you using for your portal and gateway?
Hi Mark,
We are experiencing the same issue, we are prompted for the first set of credentials but then 2nd factor doesn’t appear, the pop up screen goes white. We are using DUO for 2FA.
What type of authentication are you using for your portal and gateway (each one individually)?
Palo alto connects to DUO application gateway, it’s that what you require?
What authentication method(s) are configured on the portal? And what authentication method(s) are configured on the gateway? You should have a configuration for each one.
AD and DUO for both Portal and Gateway.
Please post a screenshot of the authentication config for both.
Hey Mark,
Any ideas how to make pre-auth/pre-login with SAML, keep the tunnel active post-login with on-demand?
I don’t want the tunnel always on, but if users do pre-auth/pre-login, I want the tunnel active after they log in.
Currently it disconnects post-login and users have to reconnect.
You should be able to accomplish this with the configuration this article. You just set the agent settings to on-demand, the user logs in with SAML using PLAP, and the connection should stay active post-logon. What are your agent settings?
Hi Mark,
I’m getting the error code 80004005 on the network setup screen. The only option it gives me is to reset the device.
https://docs.microsoft.com/answers/storage/attachments/15196-capture.jpg
Would need to know more about the configuration. Also, have you tried gathering logs before the reset?
I’ve since set the option ‘Skip AD connectivity check’ to yes and no longer receive that error, but I am now faced with a different error on device setup – Apps (0x81036502)
I will look into gathering the logs
the logs state the User-based Azure AD join failed
The machine should be doing an on-prem AD join at the initial setup and then completing a hybrid join at first logon. At what point are you receiving an error? What is the full error?
I’m receiving error 0x81036502 on the ESP under device setup.
From checking dsregcmd /status in CMD it is joining out on-prem domain but not azure AD
Device setup
Error
Security policies (1 of 1 applied)
Certificates (No setup needed)
Network connections (No setup needed)
Apps (0x81036502)
Mark,
Thanks for awesome blog. I tried all the setup from this one and remain steps from part 1. I am using perlogon method.
Only Error I am getting is at the time of app installing (under Device Setup) it says (1 of 2 Installed) and then failed cos it exceed 60 mins time out. After App fail message I continued by clicking “Continue anyways” option. Then, I can connect to GP as shown above and when I login for first time I do see the “IntuneHybridJoinHelperInstaller.ps1” created the scripts folder in C drive and runs at the first logon cos I see the pop in system notification.
My question is why its stating the app install failed? How Can I avoid?
Also , do you think I should keep or remove “IntuneHybridJoinHelperInstaller.ps1” under “Block device use until required apps are installed if they are assigned to the user/device” Enrollment options? atm I have 2 apps GP-PLAP and Intunehelper in that option.
Thanks In advance!
The helper only takes a moment to run/stage, so I’m not sure how it could be hanging. What pop-up are you seeing at first logon?
Hi Mark, great write up thank you so much for taking the time in jotting all this down for us.
I hope you can help me though, im confused as to what to do with the helper and wrapper scripts you have in order to enable GP PLAP.
Can you tell me the process? Do I just convert the GP installer to .wintuneim and add these scripts as dependencies ? Or do I upload those separately using Intune Scripts?
Sorry if this is a very basic questions I am learning.
Thanks again
I go through all of this in my first post here: https://blog.markdepalma.com/?p=528. Please take a look and let me know if you have any questions.
Does this become the GP VPN client in Windows? Or this is a separate client that shows at the windows logon screen?
I’m not exactly sure what you mean. The PLAP provider exposes the GP VPN client as an option at the logon screen, but then remains the regular GP VPN client after logon.
Nothing happens when I run PanGPS.exe -registerplap, there is no registry key created or anything. Am I missing something? Doe this not work if GP is already installed?
GP needs to be installed for this to work. PanGPS.exe is the core EXE installed by the package. Make sure you are running this as administrator.
How can you allow password changing through this if their AD account password expires or is prompted to change?
If your authentication method is Azure AD via SAML it should allow you to change your password in the logon frame.
Thanks is it just Azure AD via SAML? or also on-prem AD? If just Azure AD then that would do a writeback if enabled? Any articles/further info on that? I can’t seem to sign up on PA forums yet it’s giving me an error.
I don’t think GlobalProtect supports password changing via AD LDAP (I’ve never seen it work or seen a reference to it before). Azure AD (via SAML) of course supports this (along with other concepts like MFA and conditional access). You would need writeback enabled in a hybrid environment, yes.
You would need to follow MS documentation on the password reset pieces. This is a little different depending on if you are using password hash synchronization or pass-through authentication. You can test this without GlobalProtect simply by doing a regular Azure AD logon (ex. myapps.microsoft.com).
Currently with install GP through AP and SkippingUserESP, GP doesn’t connect until after reboot takes place. Once reboots take place, device is set for prelogin and then can login. Upon logging in, the Hybrid Join helper task runs but can’t do anything because GP is prompting to login with user and then WS1 prompt for MFA through Mobile Pass. Once logged fully to VPN, I can manually run the Hybrid Join Helper script to have the device complete the hybrid join. Given this scenario, I’m trying to determine best way to modify the scheduled task to run 10 to 15 minutes after domain connectivity is made post login. Any ideas?
I’m not sure if I’m understanding the issue. The first thing I’m not sure of is why prelogin GP VPN is failing. Why are you not able to use GP w/ PLAP to establish a VPN connection before login?
Has anyone else suddenly have this stop working for them?
Have been successfully using it for at least a year, however since Friday Autopilot ESP is failing. Have tried re packaging and starting again, but still get the error 0x8007001 on apps. As soon as we unassign GlobalProtect Autopilot works correctly!
Yes, I am on the same boat. I’ve tried all versions of GP up to version 6.3.1 and the app won’t install during autopilot. It stopped working around April 2024. Still have a ticket open with Microsoft and they can’t figure out why the app deletes after it copies the files from the staging folder over to IMECache folder. The only workaround I’ve used has been using PSADT. I am starting to think that it may be a syntax thing and whatever update Microsoft pushed out to Intune broke the script to the point that it doesn’t like something.
Have you been able to find some sort of solution?